Just doing a routine browsing this morning and i found that my Ubuntu is vulnerable with Shellshock attack. Shellshock is newly discovered security vulnerable for your bash, which means all Linux and Max are vulnerable from this security issue. Shellshock using crafted environment in bash script and gain access to your computer. This is more serious than heartbleed a while ago.To test if your Linux is vulnerable, run this script on your bash terminal:If you see a message: vulnerable … Read more...
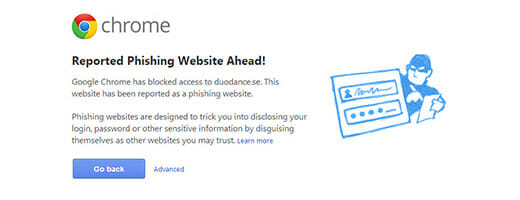
Phising Through Email Using Google Drive Link
Recently i found that some of my friends send me an email asking to see an important document in Google Drive. The title would say "Kindly Review The Uploaded Document" and here is the content of the email: Hello,please see this it's very important https://drive.google.com/ and sign in to viewIt's very importantKind regards Please see the screenshot below:The email sent to me as bcc as my contacts, so i thought it might be something important. But i'm shock when … Read more...

TimThumb Zero Day Vulnerability
TimThumb, a small php script to resize and crop images on the fly which being use by many WordPress themes (usually premium WordPress themes such as elegantthemes) all over the net. This script has been compromised with zero day vulnerability. This blog and my other blog which using TimThumb also being hacked and injected with some malicious code to the WordPress core.The compromised script was TimThumb v2.7 and below. If you are using that script, YOU MUST UPDATE IT NOW!!! I spent 3 hours … Read more...

Choose A Rememberable and Secure Password For Your Accounts
Your password is a key to all your account on the internet. All account on the internet need username and password for their basic authentication. If your password fall into wrong hand, someone can easily impersonate you while online, sign your name to online service agreements or contracts, engage in transactions, or change your account information. So, choose your password carefully and then keep it safe from others.I have a few tips for you to choose a rememberable but still a strong … Read more...

Have You Done GMail Security Checklist?
To know that your account is being hacked is the worst nightmare ever. Especially when you have a confidential information such as finance information in that account. Most of the internet account need email for communication. And even Google mail have the best security (in my humble opinion), could be compromised if you are not careful. Amit Agarwal from labnol got his GMail hacked once and he managed to recover it back after some time.Actually Google Mail has the security checklist in … Read more...

How Facebook Account Been Hacked
There have been many report that their Facebook account has been hacked by the anonymous. My cousin also report that his Facebook account being hacked even he use a fairly strong password and really keep his password safe. Even Amit Argawal from Labnol also has been hacked recently, read his post "My Facebook Account Got Hacked"."I no longer have access to my Facebook pages!", said Amit in his blog post. As the technology journalist i'm pretty sure that he used a strong password for all of … Read more...

What To Do When Your WordPress Blog Got Hacked
It's been two years i've been blogging with Wordpress. And all the knowledges and articles i wrote in this blog comes from many sources and experiences. And in 2 years blogging, i got 2 hacked attack and survive. And now if pay attention to my access log, there are still some attempt to inject the malicious code to my site. You can read my article: Someone Trying To Inject IvanKristianto.com.I'm not saying that my blog is secure and bullet proof. But i have done everything i could do, trying … Read more...

Someone Trying To Inject IvanKristianto.com
Recently i have a bad news. Beside the digital world is at war between piracy community and anti piracy company. My blog also being attack by unknown. In my opinion they are trying to find a vulnerability using a bot. They try to find a way to inject a malicious code using local file inclusion vulnerability.How to inject malicious code using local file inclusion vulnerability:Check if the website have vulnerability:If your target site have url like that then it's a big possibility … Read more...
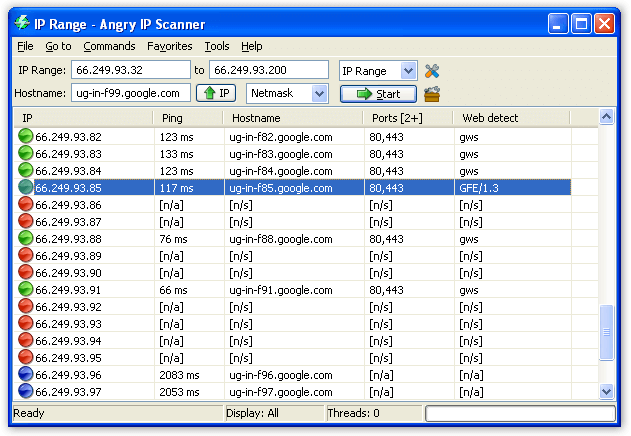
Scan All The Computer IP Addresses Inside Your Network In One Click
If you are in a large network, for example in your corporate network, in a shopping mall or any public network. You want to know how much client connect in your network and who are they, what is their IP addresses. If you use a command prompt and ping them one by one, you waste your time.To get all the ip addresses connected inside your network you can use Angry ip scanner or Advance IP Scanner by Famatech. For me they are the best tools you can use on Windows machine. And fortunately those … Read more...

Caution! Facebook Phising Attack!
Please be caution and keep your facebook account and password safe. There are lots of way to steal your Facebook account and password if you are not careful. One of them is phishing website. According to Wikipedia, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Phishing is typically carried out by e-mail or instant messaging, … Read more...
